
Proxy Servers and VPNs: What Are They Anyway?
Proxy Servers and VPNs: What Are They Anyway
I. Proxy Server: A Middleman Taking a Cut
Most people probably see the term "proxy server" and draw a blank. But if I skip the jargon and talk about VPNs and
"bypassing internet restrictions" , I bet a knowing smile would appear on your face. Today, let's dive into what
exactly a proxy server is, what tricks and functions it has, the similarities and differences between proxy servers
and VPNs, and just how safe the method of using proxy servers for bypassing restrictions really is.
Proxy Server: A Middleman Taking a Cut Lately, many people have been brainwashed by the repetitive slogan "No middlemen taking cuts" from some ads. But the proxy server actually fits perfectly into business rules because it is a specialized middleman providing services and taking its cut.
According to Wikipedia, a Proxy (also known as a network proxy) is a special network service that allows one network endpoint (usually a client) to connect indirectly to another network endpoint (usually a server) through this service. Some network devices like gateways and routers have proxy functionality. Proxy services are generally considered beneficial for protecting the privacy or security of network endpoints and preventing attacks. A computer system or other type of network endpoint that provides proxy services is called a Proxy Server.
More specifically, proxy servers can generally be divided into Forward Proxies and Reverse Proxies.
A Forward Proxy operates from the client's perspective. To retrieve content from an origin server, the client sends a request to the proxy server, specifying the target server. The proxy then forwards the request to the target server and returns the obtained content to the client. The forward proxy loop is complete.
Crucially, the forward proxy hides the real requesting client – the server doesn't know who actually made the request. Does this ring a bell? That's right, this is how most "bypassing internet restrictions" happens.
A Reverse Proxy generally operates from the server side. Requests from the network or clients are sent to the reverse proxy. Upon receiving a request, the reverse proxy determines where to send it and then relays the results back to the client. The reverse proxy loop is complete.
Similarly crucial, the reverse proxy hides the information of the internal servers. Users don't need to know which specific server provided the service; they only need to know the reverse proxy server. We can even treat the reverse proxy server as the real server. This form of proxy is often used to implement load balancing – Nginx is an excellent example of a reverse proxy server.
So, what are the specific application scenarios for these proxy servers?
Proxy Server: A Middleman Taking a Cut Lately, many people have been brainwashed by the repetitive slogan "No middlemen taking cuts" from some ads. But the proxy server actually fits perfectly into business rules because it is a specialized middleman providing services and taking its cut.
According to Wikipedia, a Proxy (also known as a network proxy) is a special network service that allows one network endpoint (usually a client) to connect indirectly to another network endpoint (usually a server) through this service. Some network devices like gateways and routers have proxy functionality. Proxy services are generally considered beneficial for protecting the privacy or security of network endpoints and preventing attacks. A computer system or other type of network endpoint that provides proxy services is called a Proxy Server.
More specifically, proxy servers can generally be divided into Forward Proxies and Reverse Proxies.
A Forward Proxy operates from the client's perspective. To retrieve content from an origin server, the client sends a request to the proxy server, specifying the target server. The proxy then forwards the request to the target server and returns the obtained content to the client. The forward proxy loop is complete.
Crucially, the forward proxy hides the real requesting client – the server doesn't know who actually made the request. Does this ring a bell? That's right, this is how most "bypassing internet restrictions" happens.
A Reverse Proxy generally operates from the server side. Requests from the network or clients are sent to the reverse proxy. Upon receiving a request, the reverse proxy determines where to send it and then relays the results back to the client. The reverse proxy loop is complete.
Similarly crucial, the reverse proxy hides the information of the internal servers. Users don't need to know which specific server provided the service; they only need to know the reverse proxy server. We can even treat the reverse proxy server as the real server. This form of proxy is often used to implement load balancing – Nginx is an excellent example of a reverse proxy server.
So, what are the specific application scenarios for these proxy servers?
II. Specific Application Scenarios for Proxy Servers
Actually, in my previous articles, I've already mentioned two key functions of proxy servers: enabling bypassing
restrictions and load balancing. But are those the only functions? Of course not. A common metaphor for a proxy
server is: a proxy server is like a big cache.
(Image representing one function of a proxy server)
Beyond the widespread use for bypassing restrictions, in the commercial world, proxy servers are typically applied in two major scenarios: increasing access speed and hiding real IPs to avoid attacks.
(Advertisement: "Too easy to get hooked, unique hidden storylines await! Heartthrob Girl" - View)
The point about proxy servers increasing access speed precisely supports the "big cache" metaphor. Typically, a proxy server sets up a large hard disk buffer zone. When information is accessed externally, it's simultaneously saved into this buffer. When another user accesses the same information, it can be read directly from the buffer and transmitted to the user, thereby increasing access speed.
Besides this scenario, there's another one that employees often dislike: companies use proxy servers to restrict employees to accessing only a few internal websites, limiting their online behavior. All under the guise of "improving employee work efficiency"...
(Image: Hiding IP via proxy to avoid hacker attacks)
Of course, information security is paramount for enterprises. Protecting corporate IP security and avoiding hacker attacks is essential. Therefore, many websites hide their real IPs using proxy servers to prevent attacks. From a corporate perspective, this is naturally a method to enhance network security. However, for law enforcement ("police uncles"), this anonymity feature of proxy servers also brings certain risks to the network. Hackers can hide their IPs, making evidence collection more difficult.
(Image representing one function of a proxy server)
Beyond the widespread use for bypassing restrictions, in the commercial world, proxy servers are typically applied in two major scenarios: increasing access speed and hiding real IPs to avoid attacks.
(Advertisement: "Too easy to get hooked, unique hidden storylines await! Heartthrob Girl" - View)
The point about proxy servers increasing access speed precisely supports the "big cache" metaphor. Typically, a proxy server sets up a large hard disk buffer zone. When information is accessed externally, it's simultaneously saved into this buffer. When another user accesses the same information, it can be read directly from the buffer and transmitted to the user, thereby increasing access speed.
Besides this scenario, there's another one that employees often dislike: companies use proxy servers to restrict employees to accessing only a few internal websites, limiting their online behavior. All under the guise of "improving employee work efficiency"...
(Image: Hiding IP via proxy to avoid hacker attacks)
Of course, information security is paramount for enterprises. Protecting corporate IP security and avoiding hacker attacks is essential. Therefore, many websites hide their real IPs using proxy servers to prevent attacks. From a corporate perspective, this is naturally a method to enhance network security. However, for law enforcement ("police uncles"), this anonymity feature of proxy servers also brings certain risks to the network. Hackers can hide their IPs, making evidence collection more difficult.
III. VPNs and Proxy Servers: Can't Tell Them Apart
As mentioned at the beginning, many people don't understand what a proxy server is but have heard of VPNs. This is largely
determined by our specific national circumstances – simply put, many people need VPNs to bypass restrictions and access
external websites. So, conceptually and technically, what are the actual differences between VPNs and proxy servers?

Conceptually, a Proxy Server is an intermediary that fetches network information on behalf of network users; it's a relay station for network information. VPN, on the other hand, stands for "Virtual Private Network".
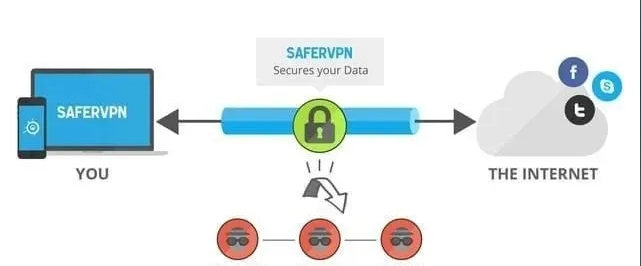
According to Wikipedia: A virtual private network is a communication method often used to connect private networks between medium to large enterprises or groups. VPN messages are transmitted over public network infrastructure (e.g., the Internet). It uses encrypted tunneling protocols to achieve security effects like confidentiality, sender authentication, and message accuracy for private communications.
In other words, a VPN is a virtually created enterprise internal private line. It establishes a dedicated network over a public network for encrypted communication. Currently, this type of VPN is a relatively common application model. Conversely, the domestic use of free or paid VPNs for bypassing restrictions constitutes a special usage pattern within VPNs. Actually, VPN is just one form of proxy server. Contrastingly, while proxy servers primarily handle internal network access to external networks, VPNs mostly solve the problem of external network access to internal networks.
Take a simple example: most company HR management systems can only be accessed successfully within the company's IP address range. If you're not on the company network, you can't open the site. But if you want to access the company's internal network (like the HR site) from an external network (like the internet), you can use a VPN to assign an internal IP address to the external network.
At the end of this section, I need to state my position:Bypassing restrictions might be appealing, but the Great Firewall is our safeguard; Information overflow can be disruptive, safe internet use is the right path.

Conceptually, a Proxy Server is an intermediary that fetches network information on behalf of network users; it's a relay station for network information. VPN, on the other hand, stands for "Virtual Private Network".

According to Wikipedia: A virtual private network is a communication method often used to connect private networks between medium to large enterprises or groups. VPN messages are transmitted over public network infrastructure (e.g., the Internet). It uses encrypted tunneling protocols to achieve security effects like confidentiality, sender authentication, and message accuracy for private communications.
In other words, a VPN is a virtually created enterprise internal private line. It establishes a dedicated network over a public network for encrypted communication. Currently, this type of VPN is a relatively common application model. Conversely, the domestic use of free or paid VPNs for bypassing restrictions constitutes a special usage pattern within VPNs. Actually, VPN is just one form of proxy server. Contrastingly, while proxy servers primarily handle internal network access to external networks, VPNs mostly solve the problem of external network access to internal networks.
Take a simple example: most company HR management systems can only be accessed successfully within the company's IP address range. If you're not on the company network, you can't open the site. But if you want to access the company's internal network (like the HR site) from an external network (like the internet), you can use a VPN to assign an internal IP address to the external network.
At the end of this section, I need to state my position:Bypassing restrictions might be appealing, but the Great Firewall is our safeguard; Information overflow can be disruptive, safe internet use is the right path.
IV. Bypassing Restrictions Might Be Appealing, But Information Security is Key
We have to admit that for various reasons, enterprises setting up VPNs for internet access or opening dedicated lines is not
uncommon. Simultaneously, all sorts of free and paid proxy servers and VPN services abound. You might not realize that
when using a proxy server, all your requests must pass through it. While it provides security and anonymity, the proxy
server also decodes the data sent through it! This means it has complete visibility into all your actions!
To improve security when using proxy servers, we need to find trustworthy servers or adopt other security measures. A common practice is to use SSL (Secure Sockets Layer) secure protocol connections. SSL was actually developed by Netscape and built into browsers. It's an encryption protocol used to compress and decompress data and return results transmitted over the network.
An SSL VPN refers to a user utilizing the Secure Socket Layer packet processing function built into their browser to connect back to the company's internal SSL VPN server. Through network packet redirection, the user can execute applications and read data from internal company servers on a remote computer. Because it uses the standard SSL to encrypt data packets in transit, it protects data security at the application layer. High-quality SSL VPN solutions ensure secure global access for enterprises.
All this talk of SSL secure protocol connections might sound complex, but you can simply understand it as the difference between HTTP and HTTPS – that extra "S" signifies a secure mode of HTTP.
Statistics show that among all proxy servers,25% modify your content, and nearly 80% do not use SSL secure protocol connections. If connected via HTTP, they can analyze your traffic and potentially steal your login credentials (including usernames and passwords)! Therefore, when surfing the web, we must always choose the HTTPS (Hypertext Transfer Protocol over Secure Socket Layer) protocol to ensure the information security of enterprises and ourselves.
Of course, besides potential threats to information security, using proxy servers can also lead to problems like ad hijacking. So, during use, we must always confirm the security of the network environment to avoid unnecessary losses.
To improve security when using proxy servers, we need to find trustworthy servers or adopt other security measures. A common practice is to use SSL (Secure Sockets Layer) secure protocol connections. SSL was actually developed by Netscape and built into browsers. It's an encryption protocol used to compress and decompress data and return results transmitted over the network.
An SSL VPN refers to a user utilizing the Secure Socket Layer packet processing function built into their browser to connect back to the company's internal SSL VPN server. Through network packet redirection, the user can execute applications and read data from internal company servers on a remote computer. Because it uses the standard SSL to encrypt data packets in transit, it protects data security at the application layer. High-quality SSL VPN solutions ensure secure global access for enterprises.
All this talk of SSL secure protocol connections might sound complex, but you can simply understand it as the difference between HTTP and HTTPS – that extra "S" signifies a secure mode of HTTP.
Statistics show that among all proxy servers,25% modify your content, and nearly 80% do not use SSL secure protocol connections. If connected via HTTP, they can analyze your traffic and potentially steal your login credentials (including usernames and passwords)! Therefore, when surfing the web, we must always choose the HTTPS (Hypertext Transfer Protocol over Secure Socket Layer) protocol to ensure the information security of enterprises and ourselves.
Of course, besides potential threats to information security, using proxy servers can also lead to problems like ad hijacking. So, during use, we must always confirm the security of the network environment to avoid unnecessary losses.
IN THIS ARTICLE
I. Proxy Server: A Middleman Taking a Cut
II. Specific Application Scenarios for Proxy Servers
III. VPNs and Proxy Servers: Can't Tell Them Apart
IV. Bypassing Restrictions Might Be Appealing, But Information Security is Key
Are you ready?
Easily collect web data using BLURPATH residential proxies
Register Now
Related Articles
Why Can't Social Media Automation Do Without Static Residential Proxies
Why Can't Social Media Automation Do Without Static Residential Proxies
Static residential proxies not only safeguard account security and stability but also enhance the efficiency
and precision of marketing efforts.
2025-06-03
Getting Started with SOCKS Proxies: What is SOCKS5 and Why Use It
Getting Started with SOCKS Proxies: What is SOCKS5 and Why Use It
Now that we understand proxies broadly, let's focus on a specific type—SOCKS, particularly the SOCKS5 variant.
2025-06-04
What's the Difference Between HTTP Proxy and SOCKS5 Proxy
What's the Difference Between HTTP Proxy and SOCKS5 Proxy
While both HTTP proxies and SOCKS5 proxies serve similar purposes, they differ in protocol support, speed, and
setup complexity.
2025-06-05